For several days, the Cybercrime Act, which was passed in 2015 and revised in 2024, has been debated on various digital and physical forums. The Act became the focus of discussions after the Central Bank of Nigeria announced that some electronic bank transactions should be charged and remitted as a cybersecurity levy. As arguments and counterarguments over the new levy persist, our analyst examined the Act and the inherent ideological orientations that underpin the execution of the tax deduction directive.
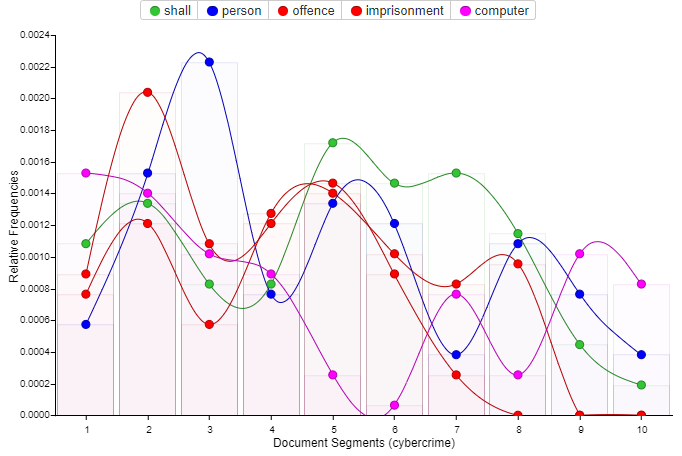
The Cybercrime Act of 2015 (pdf) addresses the prohibition, prevention, detection, reaction, investigation, and prosecution of cybercrimes, as well as other connected issues. Nigeria hopes to do this in order to guarantee a sustainable and safe cyberspace comparable to that which is available in other nations. Using a corpus analysis approach, our analyst examined the Act and found that it was composed of 15,699 words, with three instances of levy and twelve instances of transactions. The most frequently used terms, according to analysis, are shall (166), person (161), offence (126), computer (126) and imprisonment (123).
The data in Exhibit 1 further reveals material and non-material objects associated with the use of the key terms. The use of “shall” is intertwined with “person,” “offence”, “computer,” and “imprisonment.” This reaffirms the long-held belief that in the legal field and practice, words like “shall” and “will” are strategic linguistic devices for helping law followers and enforcers understand the gravity of what they must do to effectively implement provisions in various sections of any Act.
Register for Tekedia Mini-MBA edition 19 (Feb 9 – May 2, 2026): big discounts for early bird.
Tekedia AI in Business Masterclass opens registrations.
Join Tekedia Capital Syndicate and co-invest in great global startups.
Register for Tekedia AI Lab: From Technical Design to Deployment (next edition begins Jan 24 2026).
Our analyst notes that having a computer as a keyword at the centre of the Act indicates the prioritisation of it as a mechanical material object people need to use to commit varied cybercrimes. And at the same time, use for addressing issues that occurred after by the Act implementers.
Exhibit 1: The key material-knot of the Act
Exhibit 2: Circlic of key material-knot with cybercrime
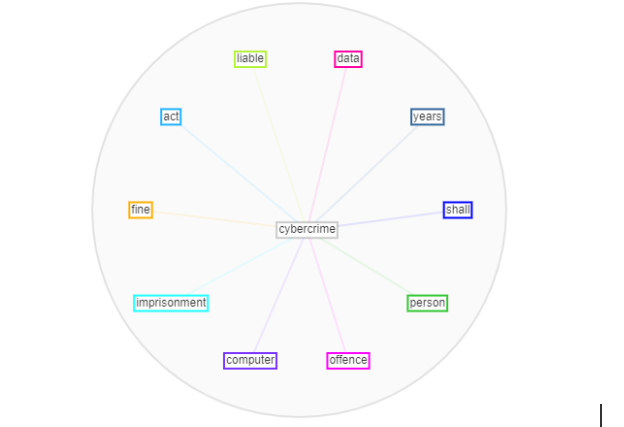
In Exhibit 2, it emerged that cybercrime is a keyword in the Act corpus that is connected with words that indicate actions needed and words that represent objects that would be used to judge people who violated provisions in various sections of the Act. The core processes for implementing the Act from a financial standpoint are mostly spelled out in Section 44. Subsection (1) of this section notes that “there is established a Fund, which shall be known as the National Cyber Security Fund (in this Act referred to as “The Fund”). This provision implies that maintaining a safe and secure cyberspace will be difficult if a special fund is not established. However, given the amount of existing sources from which the government may draw, our analyst believes that the creation of the Fund would create an additional burden on individuals, firms, and organisations that are expected to be key contributor to the Fund.
Subsection (2) of the same section clearly states the collection and deposit of the Fund in the Central Bank of Nigeria. In this regard, paying and remitting the Fund are intertwined with the human and mechanical processes that would be deployed. This becomes clear when one looks at paragraph (a) of subsection (2), which states, “A levy of 0.005 of all electronic transactions by the businesses specified in the second schedule to this Act,” where it is evident that people and businesses are the key contributors from a banking transaction perspective.
In what appears to be a balanced strategic choice game of getting the needed funds, paragraph (b) stresses grants-in-aid and assistance from donor, bilateral and multilateral agencies; (c) all other sums accruing to the Fund by way of gifts, endowments, bequest or other voluntary contributions by persons and organisations: provided that the terms and conditions attached to such gifts, endowments, bequest or contributions will not jeopardise the functions of the Agency.
Exhibit 3: Relative frequency of the key material-knot with cybercrime